Welcome to ZirconTech’s Most Viewed Articles page, where we showcase the most engaging and thought-provoking content from our esteemed technology platform. As a leading provider of cutting-edge solutions and innovations, ZirconTech is committed to empowering businesses and individuals with the latest trends, insights, and advancements in the tech industry. Whether you’re a seasoned professional, an aspiring entrepreneur, or simply a curious mind eager to explore the frontiers of technology, this curated selection of our most popular articles offers a gateway to a world of knowledge and inspiration. From AI and blockchain to cybersecurity and IoT, dive into our featured articles and embark on a journey of discovery, unraveling the exciting possibilities that lie at the intersection of technology and human potential. Join us as we explore the transformative power of innovation and uncover the future that awaits us in the digital age.
-
Optimizing DynamoDB with GraphQL APIs and AWS AppSync
As applications increasingly demand flexibility and responsiveness, traditional methods of data handling can fall short. This article explores the powerful combination of DynamoDB, GraphQL, and AWS AppSync, highlighting their features, advantages, and best practices for integration. Understanding GraphQL GraphQL is a query language for APIs and a runtime for fulfilling those queries with existing data.…
-
Streamlining Your Build Process with AWS CodeBuild
The build process plays a crucial role in ensuring code quality and preparing applications for deployment in software development. Once developers commit their code to a source repository, the next critical step is building the application. But what exactly does a successful build entail? A build takes the source code, compiles it, retrieves dependency packages…
-
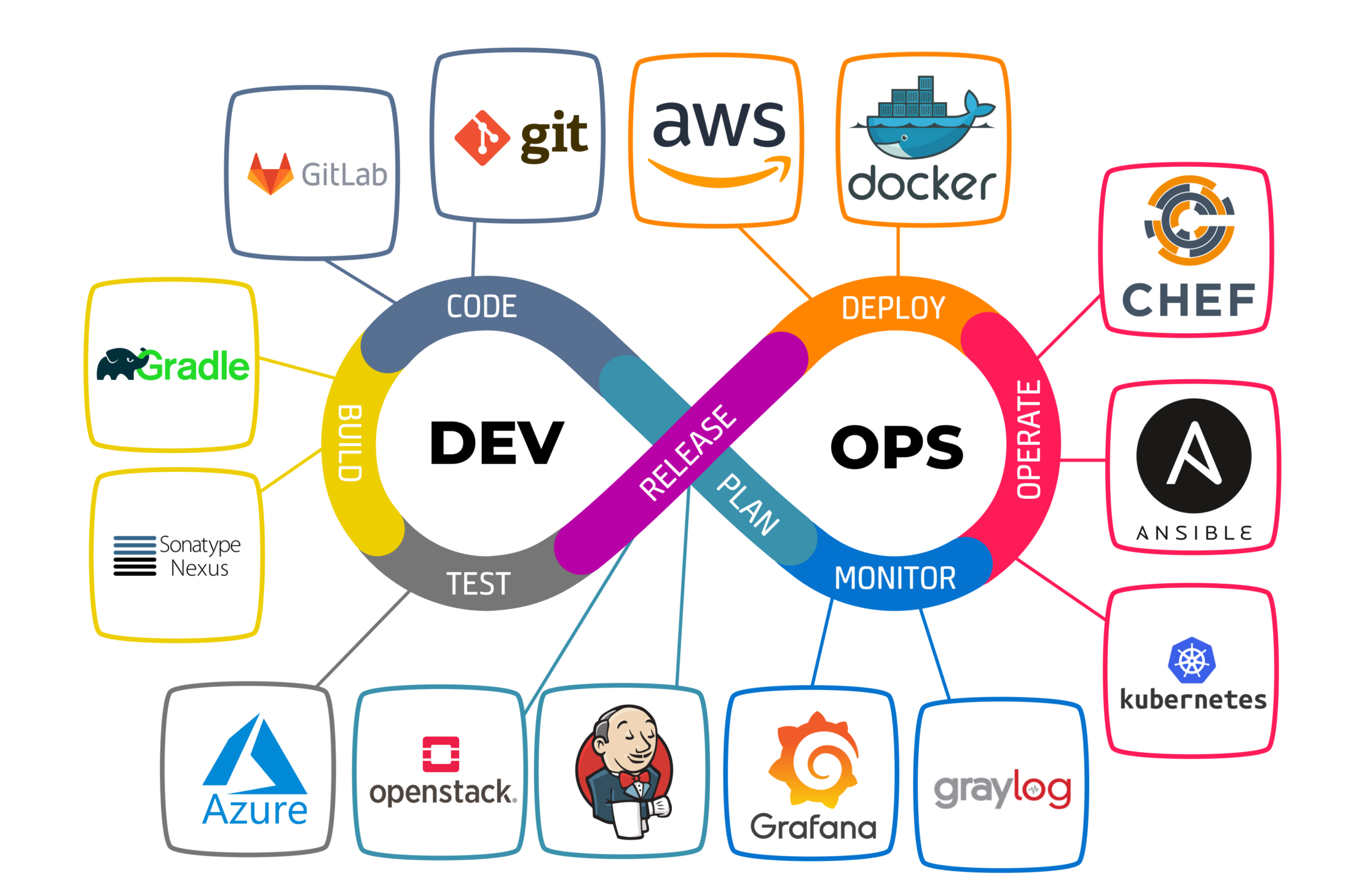
Understanding DevOps: A Bridge Between Development and Operations
Collaboration between developers and operations teams is crucial to ensure smooth, successful deployments. Traditionally, these two teams worked separately—developers focused on building new features while operations handled the deployment and maintenance. However, this divide often leads to frustration and inefficiencies when things go wrong in production environments. DevOps seeks to bridge that gap, fostering collaboration,…
-
Optimizing Storage Costs on AWS: A Strategic Approach to Data Management
Platforms like Canva have witnessed astronomical growth since their inception. Serving over 100 million active monthly users and hosting more than 15 billion designs, the sheer scale of data managed is staggering. With this growth comes the challenge of managing and optimizing the storage of over 230 petabytes of data on AWS, specifically using Amazon…
-
Azure Cost Optimization: Strategies and Best Practices for 2024
Managing costs effectively is a critical component for businesses leveraging platforms like Microsoft Azure. As organizations continue to scale their cloud infrastructure, it’s essential to optimize spending while ensuring that performance and availability meet business needs. This article gets into updated strategies for Azure cost optimization, providing a comprehensive guide for businesses aiming to reduce…
-
Driving Financial Resilience: Cost Optimization Strategies for Startups on Google Cloud
As the adoption of cloud computing continues to rise exponentially, startups and organizations are increasingly focused on how to optimize their cloud costs while maximizing the value they derive from their investments. In today’s competitive landscape, managing cloud expenses effectively is not just about reducing costs—it’s about driving financial resilience and ensuring that every dollar…
-
Mastering Cloud Cost Optimization: Strategies for Efficient Cloud Spending
As organizations increasingly migrate to public cloud infrastructures, the quest for cost optimization becomes paramount. Managing expenses related to Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) is crucial to maintain a balance between performance and cost-effectiveness. With cloud spending growing rapidly, optimizing these costs can lead to significant savings and more…
-
How ZirconTech’s Blockchain & Web3 Accelerators Drive Circular Economy and Supply Chain Traceability
Addressing Supply Chain Traceability Challenges with Blockchain & Web3 Accelerators In today’s world, the shift towards a circular economy is more critical than ever. Circular supply chains are essential to sustainable business models, yet they face significant hurdles, such as transparency issues, inefficient resource management, and fragmented data handling. These challenges result in increased operational…
-
Modernization pathways in AWS
Making something modern and, more importantly, keeping it modern is a journey, a constant change. This applies to many things in life, and software is no exception. Let’s embark on this path. Imagine that after an overdose of listening to AC/DC, we wanted to create a website with unpublished photos of concerts in music history.…
-
The Importance of Document Integrity in Airlines
Introduction to Document Integrity Challenges in Airlines Every day, airlines manage a vast array of critical records — from passenger information and flight data to maintenance logs and crew schedules. The accuracy and security of these documents are not just a matter of regulatory compliance, but also crucial for safety and efficient operation. Consider the…